Security Enablement on NXP Microcontrollers
With the rapid emergence of cloud connected AI devices in industrial automation, smart city, smart home and vehicular automation have become part of all our lives. With enormous numbers of wired and wireless devices connected in the world, security becomes a necessity and should be considered at the early stages of a product design. To harness the advanced hardware security features embedded in NXP’s devices, security enablement is provided in MCUXpresso suite of software and tools for product designs to meet these challenges and associated industrial standards. The MCUXpresso tools enable products to be deployed with the following security features:
- Secure Programming and Device Provisioning
- Security Certifications
- Over-The-Air (OTA) update
- Debug authentication
- Data protection through Runtime security
Software Details
Features
-
Secure Programming and Device Provisioning
- On-chip memory programming
- Code signing and encryption
- One-time programmable (OTP) / e-fuse register programming
- Secure binary image generation
- Secure bootloader configuration
- Security Certifications
-
Over-The-Air (OTA) Update / Over Wired Network Update
- Manage cloud connected devices
- Deploy software update
-
Debug Authentication
- Platform Security Architecture (PSA) compliant
- Prevent unauthorized debug access
-
Runtime Security
- Detect exploitations and vulnerabilities
- Establish secure data transfer channel
- Arm® TrustZone®
- Trusted Firmware-M (TF-M)
- Trusted Execution Environment (TEE)
Secure Programming and Device Provisioning
Secure programming involves on-chip memory programming, code signing and encryption, one-time programmable (OTP)/e-fuse register programming, secure binary image generation and secure bootloader configuration. Secure Provisioning SDK (SPSDK) and MCUXpresso Secure Provisioning (SEC) tools are designed for developers and manufacturers to implement secure programming on NXP’s ARM based microcontrollers. Software IP and secret keys are the essential assets of OEMs. To prevent these assets from being stolen during the manufacturing process, NXP’s trust provisioning solutions enable software IP protection, secure credentials injection and production quantity control. Device HSM Trust Provisioning, EdgeLock® 2GO and Smart Card Trust Provisioning are designed for device provisioning in an unsecured or untrusted production environment.
Security Certifications
Platform Security Architecture (PSA) and Security Evaluation Standard for IoT Platforms (SESIP) which are initiatives from ARM and GlobalPlatform respectively, define industrial standards for IoT security. Both standards set a universal baseline of requirements and help IoT device makers build their products based on some foundational security components provided by NXP’s microcontrollers and processors.
Below is the list of approval NXP devices:
| Device Name | Certification | Level |
|---|---|---|
| i.MX RT500 | PSA | 1 |
| i.MX RT600 | PSA | 1 |
| LPC55S00 | PSA | 1 |
| LPC55S16 | PSA | 2 |
| LPC55S36 | PSA and SESIP | 3 |
| i.MX RT1050 | PSA | 1 |
| i.MX RT1060 | PSA | 1 |
| Layerscape Series | PSA | 1 |
| 1.MX 7ULP1 | PSA | 1 |
| i.MX 8M Mini | PSA | 1 |
| i.MX 8M Nano | PSA | 1 |
| i.MX 8M | PSA | 1 |
| i.MX 8M Plus | PSA | 1 |
| i.MX 8QuadXPlus | PSA | 1 |
| i.MX 8QM | PSA | 1 |
Other Security Technologies
OTA Update
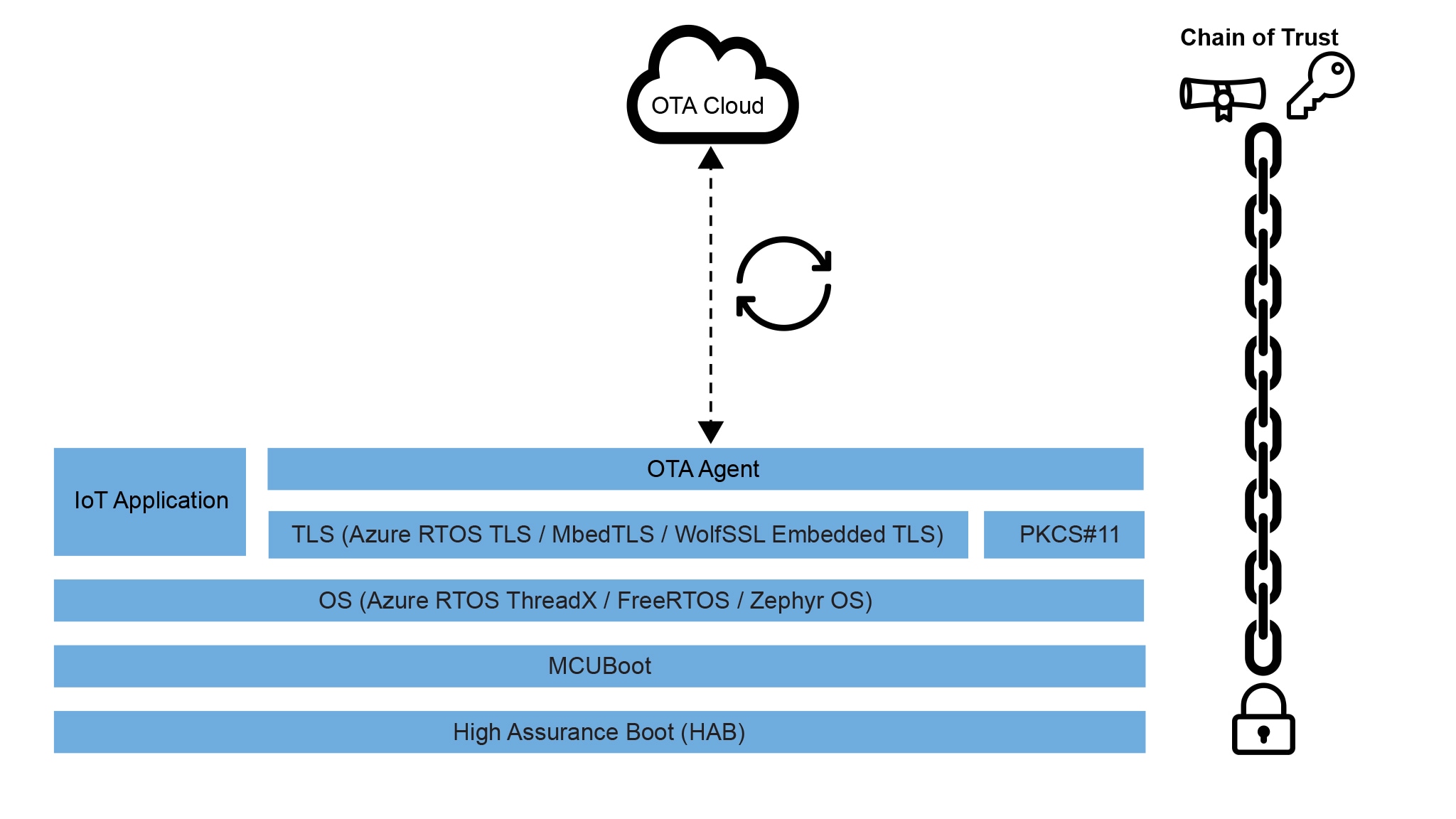
Over-The-Air (OTA) or over wired network updates allow IoT device makers to manage their cloud connected devices and deploy software updates when necessary. A secure OTA update framework is critical, as it ensures the chain of trust of the entire system, from NXP's device immutable based boot code to the OTA agent which interacts with device management services. NXP and its partners collaborate to provide secure OTA framework implementation based on NXP's security-enabled microcontrollers and processors, providing ready-to-use implementations that can be customized for specific customer needs.
MCUXpresso SDK provides example codes of the AWS OTA and Microsoft ADU reference designs. NXP Partners Ecolux and Goliath also provide secure OTA solutions on NXP’s microcontrollers and application processors.
Debug Authentication
Debug authentication enables failure analysis support and diagnosis without compromising security and meeting PSA security certification requirements. Securing the debug interface of NXP Armv8-M based devices makes sure only authorized debug access is allowed to certain parts of firmware and hardware. The Secure Provisioning SDK (SPSDK) and MCUXpresso Secure Provisioning (SEC) tools are designed for developers and manufacturers to access the debug authentication function on NXP’s microcontrollers.
Runtime Security
Embedding runtime security software in cloud connected devices is a necessity to prevent denial of service attacks, prevent malware insertion, and to protect user data and product IP. It helps protecting devices by securing connections between cloud services and edge devices, routers and data communication links. MCUXpresso SDK provides options for MbedTLS libraries from ARM and Microsoft NetXDuo to provide secure TLS stacks for cloud connected applications, with WolfSSL also providing TLS libraries to secure communication links for data transfer. WolfSSL also offer specialized support and several other security protocol stacks enabling developers to ensure a secure communication channel is established for data transfer. Detecting exploitations and vulnerabilities is a valuable capability to protect edge connected products. NXP Partner Sternum provides a runtime protection solution that prevents exploitations and avoid regular patching. Trusted Firmware-M (TF-M) provides a platform security architecture reference implementation aligning with PSA certified requirements for Arm v8-M and Armv8.1-M processors. It leverages Arm TrustZone technology and forms the foundations of a Trusted Execution Environment (TEE). MCUXpresso SDK provides TF-M example implementations, as used to achieve PSA certification. Several NXP microcontrollers with Arm v8-M cores also include the Trustzone feature, with the concept of hardware-enforced secure and non-secure code execution. To augment this, additional hardware checkers are included in these devices to check for unauthorized accesses happening from unauthorized code. MCUXpresso Config Tool supports generation register configurations for these Trusted Execution Environment (TEE) features on NXP’s microcontrollers.
Training
5 trainings

