As intelligence becomes more and more integrated into things that we interact
with, a growing number of new opportunities are arising for secure
transactions such as payment through our appliances, vehicles and homes.

Linux Point of Sale (POS) Reader Solution
Devices that can accept payment demand stringent security and interoperability
capabilities.
NXP’s Linux Card Reader
solution brings together a variety of technologies into one embedded system
that is designed to meet these needs.
The Linux operating system is the most widely used OS for payment terminals.
Due to the open source nature of this OS, it offers many benefits with regards
to its extensive ecosystem support. However, some vulnerabilities still exist
which must be mitigated for a secure design.
Payment Architectures
Payment terminal architectures can be categorized into three types:
The least complex payment devices support form factors such as secure pin
pads, mobile point-of -sale (mPOS) devices that attach to a Smart Phone or a
portable battery-powered point-of-sale device. These are commonly built on an
MCU architecture, such as an Arm® Cortex-M CPU running at greater than
100MHz. The embedded memory for such devices varies based on the end device
functionality, ranging from 256KB – 1M of embedded flash and up to
256KB of SRAM.
Figure 1 details the most complete representation of this
MCU-based architecture with all device functionality supported.
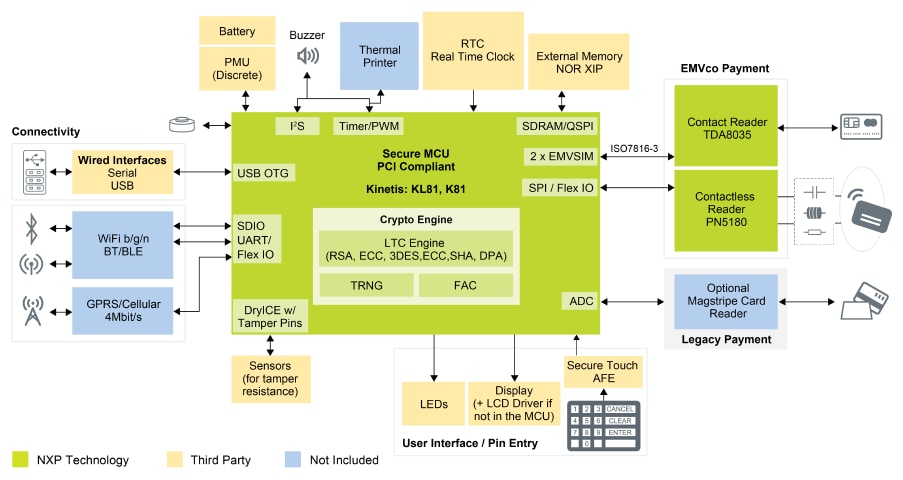
Figure 1: MCU for payment
The human machine interface (HMI) functions include the pin pad, display,
status LEDs and buzzer. There is connectivity via wired or wireless
interfaces, system clocks and power and the card reader interfaces. The card
reader interfaces can include a magnetic stripe, contact cards and contactless
cards or smart phones using near field communications (NFC).
In some instances, the point-of-sale (POS) device may require high processing
to run high-definition video and to display advertising – in this case,
a split architecture can be deployed. This is essentially taking the MCU
system architecture shown in Figure 1 and adding a high-end processor that
would typically be found in a tablet or a smartphone as shown in Figure 2.
The applications processor will typically be running Android, which is built
on top of the Linux OS.
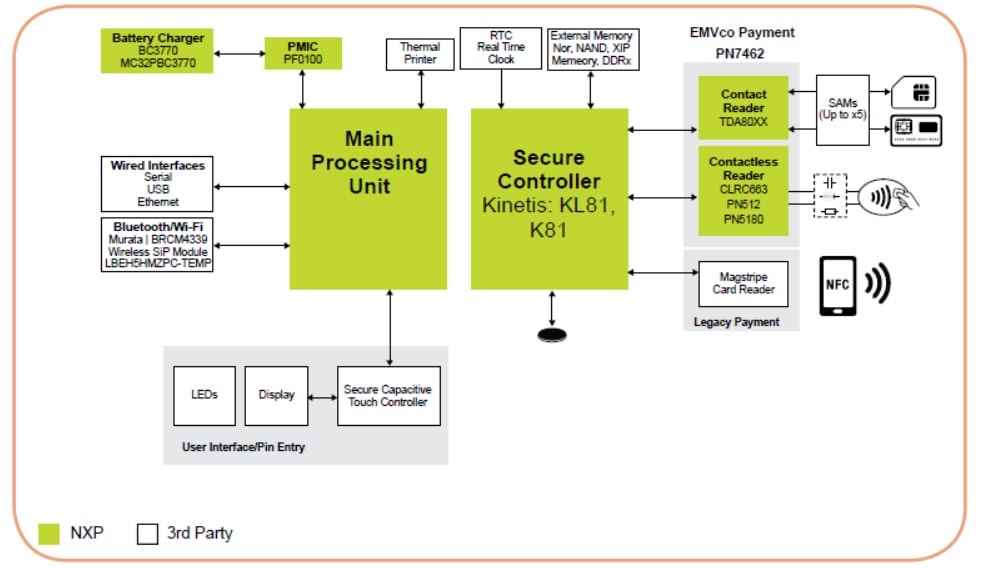
Figure 2: Split Architecture Payment
The secure MCU in this architecture has the task of communicating
with contact and contactless readers, as well as performing the bulk of
the functionality to support the security of the end device. The high-end
applications processor provides the multimedia functionality. For both of the
previous architectures, the
RTOS Card Reader solution
provides the basis for a speedy design.
The third architecture addresses the most common POS form factors of table top
and portable POS devices, based on applications processors running the Linux
operating system. The functionality provided by this architecture can range,
just as the microcontroller-based systems. These can support mPOS designs, and
scale up to embedded systems that work with their own modems to complete
payment transactions.
Arm Cortex-A® CPUs are needed to support the Linux operating system; they
offer more expandability to the end user. This type of device allows merchant
acquirer customizations and can work with payment network infrastructures that
are already in place. Leveraging the Linux OS, this architecture provides a
path to richer displays and more performance.
Addressing Security Standards
Due to the standards for securing consumer payment card transactions, not
every embedded processor or configuration of Linux works in a payment
device. Payment terminals must follow Payment Card Industry Pin Transaction
Security standards (PCI PTS). With the PCI PTS guidelines, the embedded system
is designed to meet the protection profile mandated for the end
application of supporting payment.
The PCI PTS standard identifies the pin pad, card interfaces and system
integrity as functions that require the highest security protection.
NXP’s
Linux Card Reader solution
implements a Trusted Execution Environment (TEE) which manages and protects
sensitive user interfaces and their data.
NXP’s low energy i.MX6UL processor with Arm TrustZone® supports
four processor states to logically isolate resources inside the system. There
are user and privileged modes for the secure processor state and separate
user/privileged modes for the normal processor state. These states are
logically isolated from each other to reduce the attack surface for the Secure
World services.
Software running in the Normal World does not have access to memory and
protected peripherals in the Secure World. For the Linux Card Reader, all
functions related to maintaining the security of the payment system are
partitioned into the TEE as shown in the following diagram:
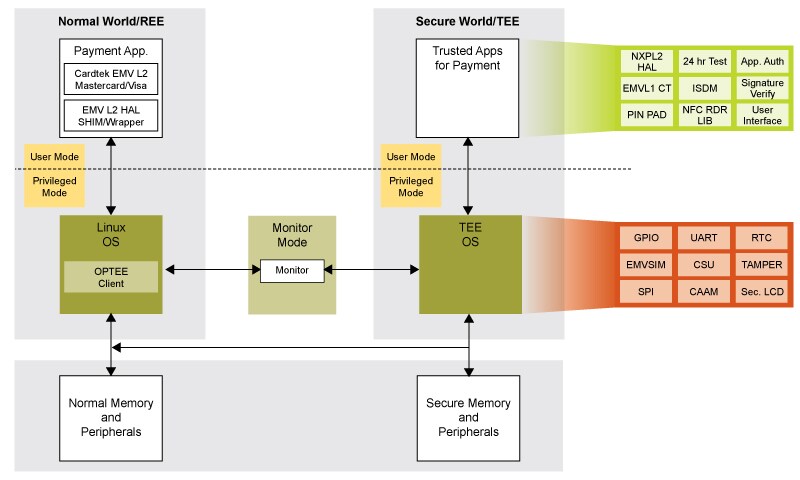
Figure 3: Trusted Execution for payment using Arm TrustZone
The TEE is made up of an application layer, which runs in Secure World-User
Mode (top right of the diagram) and the TEE OS which is running in Secure
World-Privileged Mode (bottom right of the diagram). The components in
the TEE OS are the peripheral drivers for the protected peripherals –
these include components such as GPIO, LCD and the Cryptographic Assurance
and Acceleration Module (CAAM). The TEE OS components are static as they
are all loaded during boot time. Sitting above the TEE OS components are the
trusted applications which are dynamically loaded as they are utilized. The
trusted applications are logically isolated from one another as well as from
Normal World.
For the payment use case, there are trusted applications for self-testing
every 24 hours, taking in the user PIN and reading the payment cards. As we
can see from the diagram, a TEE provides the framework for development of
secure applications, but every device will require specific capabilities
related to the services it provides.
To bolster security, the Linux Point-of-Sale Card Reader solution from NXP
includes a security manager trusted application. The Inter-Security Domain
Manager (ISDM) component learns the payment card transaction flows and
protects against unintended operation. A decision tree based on a supervised
learning phase during development is part of the trusted application which
resides inside the TEE. This provides strong logical security protection
necessary for supporting applications such as payment card readers.
The Linux Card Reader Solution brings together a secure and reliable system
architecture along with certification reports to launch secure embedded
designs. Additionally, there are components that ensure compliance to EMVCo
standards. To learn more about this design, visit:
Linux Point of Sale (POS) Reader.








