A decade ago Samuel L. Jackson’s character in Snakes on a Plane expressed his displeasure with the titular quandary. I feel the same way about malicious software running on internet-connected things like security-camera recorders. Such malware running on hundreds of thousands of devices in October 2016 rendered a swath of the Internet inaccessible.
You can’t say that I didn’t warn you. In 2015 I delivered a talk called “Halting the Thingbot Army with Secure Gateways.” In this talk, I highlighted the benefit of inserting a secure gateway between insecure things and the Internet. It mostly comes down to expectations: we expect a secure gateway to maintain the confidentiality, integrity, availability of the network and nodes behind it whereas we expect internet-connected things to be “crap.”
It’s not that many of these things couldn’t be intrinsically secure. The capabilities of unconstrained things—those that run a high-level operating system—that enable them to run malware are the same capabilities that can keep the malware off in the first place. Until countries have a liability and regulatory framework to address their vulnerabilities, these things will remain insecure. In the meantime, this blog entry will discuss the October attacks. The next entry will go into more detail about platform trust.
In October, malefactors infected vulnerable consumer electronics such as IP cameras and digital video recorders with a simple program called Mirai. Mirai disabled these devices, harnessing them to send a ton of malicious network traffic to overload the DNS servers operated by a company called Dyn. Once running, Mirai kills every other process, bricking the device. Next, it repeatedly does two things: reproduce and attack, as the figure below shows. It reproduces by scanning the Internet for other vulnerable systems and copying itself to these systems. It attacks by calling a command-and-control (CnC) server over the Internet to get a list of targets, then by flooding these targets with packets to deny targets’ ability to service legitimate requests.
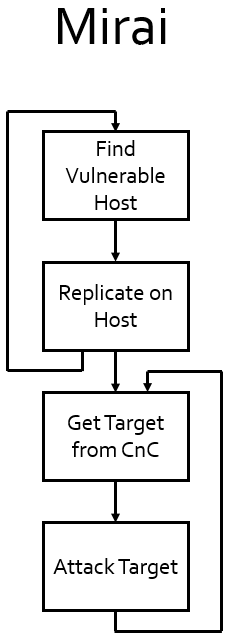
Mirai’s victimized hosts were vulnerable because they permitted remote access, had known and unchangeable passwords and would execute any code they were told to run. In other words, they were crap. Victimized hosts, which were mainly video cameras and digital video recorders, also sat directly on the Internet. Consumers want remote access to their video, so they put these devices in their home gateway’s DMZ. This keeps a victimized device from compromising other systems on the consumers’ LANs but doesn’t protect the rest of the world.
It would have been better for these consumers to open a single hole for video service. Unfortunately, asking consumers to be more careful isn’t a reasonable request owing to their limited network-security expertise and to gateways’ awkward user interfaces. Moreover, consumers didn’t know the victimized hosts had other network services running with insecure passwords.
Here’s where a secure gateway could have helped. It could do things like:
- Requiring connections initiated outside the home to home-hosted devices to be made over a VPN. Among other benefits, a VPN forces remote users to authenticate, preventing malware from connecting to flawed devices behind the gateway. Some home gateways already implement VPN servers, and all modern smartphones have built-in VPN clients.
- Filtering network traffic to maintain the availability of the network and nodes on it. The simplest approach would be to rate-limit services, such as DNS requests harnessed in Mirai’s attack on Dyn. Another approach would be to inspect packets for malware, provided that the gateway had a set of malware signatures. A smarter approach would use a newer technique called user/entity behavior analysis (UEBA) that uses artificial intelligence to learn what normal network traffic is and flag or block traffic that does not behave normally.
- Implement a hardware trust architecture to ensure the integrity of the gateway itself. This requires certain features in the system-on-a-chip at the heart of the gateway, and is the subject of my next blog entry.
In summary, just as it would have been a lot easier to keep the snakes off the plane to begin with than to deal with the aftermath of their infiltration, we will all be a lot better off securing the Internet of things.





