PLCs are an essential part of any production line and as we move deeper into
the fourth industrial revolution, more internet-connected sensors and systems
are interfacing with PLCs. This exposes the complete system to cyber-attacks
that are difficult to predict and can lead to complete system failure, life
endangerment and financial loss. To mitigate this, designers should take
preventative measures at both the hardware and software level to protect PLCs
and other connected devices in the factory.
Common Security Attacks
Table 1. shows common security attacks on a PLC system including local attacks
such as PLC reprogramming via a flash drive or SD card and remote attacks such
as man-in-the-middle that hide potential faults in production. For example, in
a food and beverage manufacturing facility producing ingredients for chocolate
or baking, it is essential to track all chemicals in a mixture and monitor key
events such as a faulty boiler. A man-in-the-middle attack that hides
potential faults can result in erroneous mixtures unbeknownst to the operator.
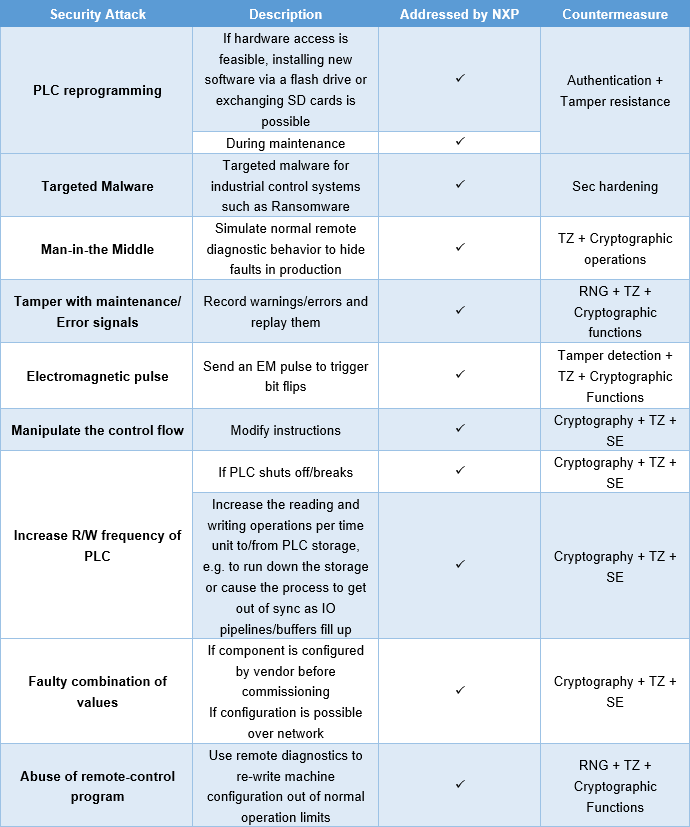
Table 1. Micro Safety PLC Security Attacks
PLC Design with Security Features
NXP has developed a broad portfolio of scalable security solutions that
provide a foundation for achieving the most effective security levels based on
the potential security attacks on a system. Figure 1. shows a Micro Safety PLC
solution that addresses the attacks shown in Table 1.
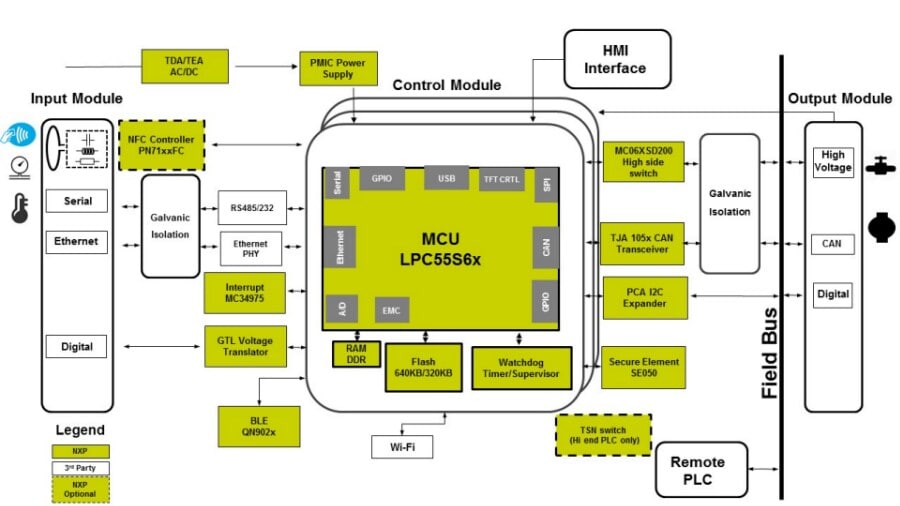
Figure 1. Micro Safety PLC Block Diagram
The LPC55S6x MCU incorporates software-based security based on Arm TrustZone
(TZ), which enables a secure and isolated execution environment that handles
trusted operations including communication to external memory and software
updates. To further isolate protected operations, the SE050 secure element
provides support of main TPM functionalities including physical isolation that
protects keys, tamper resistant protection and software authentication.
It also creates a secure channel for data transfer to the MCU.
The combination of the LPC55S6x MCU and SE050 secure element provide a
countermeasure to maximize security and maintain system integrity throughout
the lifecycle of the PLC. This minimizes system downtime and critical
information leakage that promotes safety and quality.
Additional steps can be taken to mitigate security attacks such as regular
updates to antivirus software to reduce malware injection instances,
appropriately managed access level to PLCs by personnel and only allowing
certain PCs to be used for programming.
Additional Resources
Click here to learn more about NXP factory automation solutions
Learn more about NXP security solutions
Stuck on something? Get answers to your questions on our community page






