Author

NXP
At NXP, innovation is always now, but our focus is always the future. Our dedicated team of experts is united by a passion to make everyday life more remarkable through technologies that continually redefine life as we know it.

As part of a continuing blog series on mobile government (mGov), we’ve discussed the expansion of online access to government services, and how derived credentials, a form of digital ID, can make it safer to use mGov services.
In this blog, we look at the emerging discipline of credential management, which ensures a properly derived and stored credential, and the types of applications that can benefit from using derived credentials. We begin by looking at the best way to derive a digital credential.
Smartcard eIDs provide the foundation
The smoothest transition to mobile access begins with the proven, verified electronic IDs (eIDs) associated with smartcards. This is because smart card eIDs are governed by national or internationally recognized standards and have proven themselves, in years of use in billions of authentications, to be a trusted way to identify a person. The digital credentials derived from smart card eIDs reflect this high level of trust and provide a sound basis for mobile access.
The embedded secure elements (eSEs) used to support derived credentials are another important part of the security picture, since they’re compatible with existing contactless smart card infrastructures (including those that use MIFARE or NFC), and can be authenticated using in-place methods. Built-in compatibility with the existing infrastructure also helps simplify the deployment and lowers the cost of ownership.
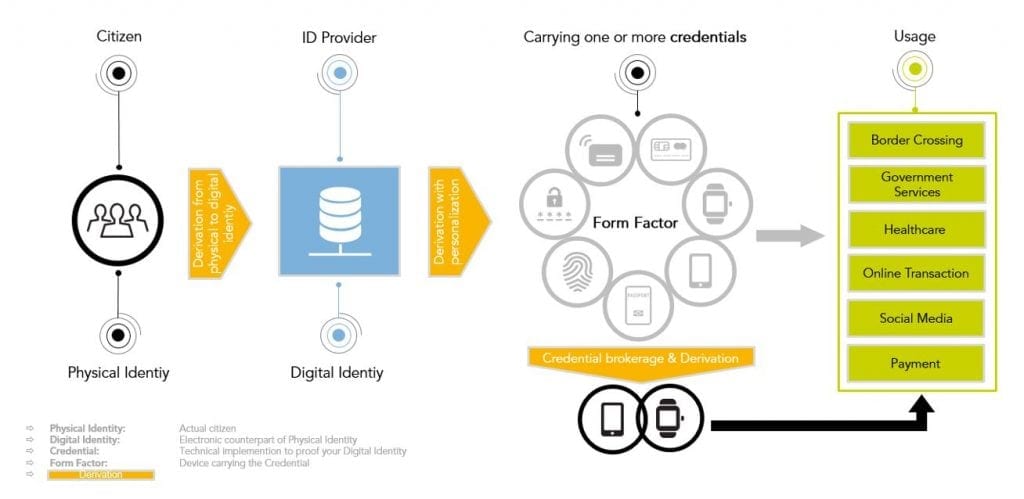
Having established an infrastructure for trusted ID services that are based on derived credentials, governments can get closer to the ideal of creating a single-entry point for multiple services, since the new infrastructure makes it possible to issue one ID that fits every application. Using a single ID to access multiple services, in what’s referred to as “federated” ID management, is something private organizations are pursuing, too, since the approach enables secure use of private digital information while extending the service offering.
One ID, many uses
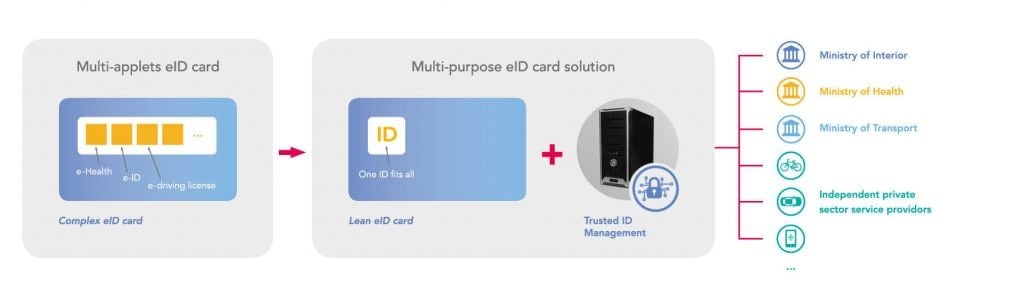
As an example of using one digital credential to simplify access to multiple services, consider a smartcard-based eID program that already includes two applets, one for a national ID and one for a health card. Adding a third applet, for a driver’s license, makes the smart card design more complex and means more stakeholders must align and agree on a suitable card profile.
With an infrastructure for properly derived credentials and a flexible authentication platform, however, these design constraints are essentially removed. A single ID can be securely linked to multiple applications, for use with any number of public and private services. The initial card launch can be quick, with new use cases added over time. The total cost of ownership goes down, while the number of options available to citizens goes up.
The derived credential can be used in much the same way traditional IDs are used, but in a mobile context. In the case of the driver’s license, for example, the derived mobile driving license might be used to reserve a rental car, to verify the driver’s authorization to operate the vehicle. The derived credential from a national ID can serve as verification of residency when applying to open a bank account, initiate utility service to a new apartment or join the local library. In similar fashion, the derived credential from a healthcard might be used to verify medical information, such as a prescription for medication or corrective lenses, when using an online pharmacy or ordering a pair of eyeglasses. Derived credentials offer a unique combination of flexibility and security, making it possible to transition just about any service, public or private, to the mobile environment.
Context-aware authentication
In many of today’s online applications, developers are forced to make a tradeoff between security and convenience. As the level of protection increases, ease of use tends to go down, since the authentication process becomes more complex. Using derived credentials in mobile devices promises to eliminate this trade-off between security and convenience, since the mobile format enables next-generation ID methods that are both secure yet easy to use because they are context aware. That is, the authentication method used by the back-end system takes into account factors like who the user is, what they are requesting, how the user is connected, the time of day and where the user is located. With context awareness, the authentication process might use one set of requirements when the access request comes from a network inside a government office, but a different set when it comes from a public Wi-Fi.
Operating in response to current conditions, these context-aware methods promise to optimize security, convenience and cost. The identification method can vary depending on the device and its specific features. For example, if the device is equipped with a biometric sensor that reads fingerprints or recognizes a face or voice, then the authentication method can use the biometric. If the device doesn’t have a biometric, then a PIN number, a Transaction Authentication Number (TAN), or a password can be used as the basis for authentication.
The added level of flexibility afforded by derived credentials and context-aware authentication means it’s easier to choose the right level of security for each situation. With high-stakes applications, such as access to health records, for example, multi-factor authentication can be used to reach the necessary level of security, but with applications that present a lower risk, a less sophisticated authentication method can lower the technology overhead – without compromising privacy or security.
NXP’s approach to derived credentials for mGov
At NXP, we’re building on our number-one position as a supplier of silicon solutions for eGov to support the trend toward mGov. We are already a leading supplier of eSEs to the smartphone industry, and a recognized innovator in the secure services that rely on eSEs for protection and are using that experience to build solutions for other mobile devices and mGov applications. We’re also creating a service platform that will provide our customers with an infrastructure for digital authentication supporting various credential types.
Using eID hardware as a starting point, the NXP platform supports an easy design and deployment of secure authentication services for mobile applications, and will help developers migrate multi-application eID operation into the mobile space.
Go a level deeper
To learn more about our work in this area, visit the eGov section of our website or contact your local sales office.
Related links
NXP blog: Paving the way for digital identities and mobile eGov access
Tags: Security, Technologies

At NXP, innovation is always now, but our focus is always the future. Our dedicated team of experts is united by a passion to make everyday life more remarkable through technologies that continually redefine life as we know it.

April 11, 2019
by Kurt Bischof

September 11, 2019
by Mahdi Mekic

October 17, 2019
by Tim Daly