Author

NXP
At NXP, innovation is always now, but our focus is always the future. Our dedicated team of experts is united by a passion to make everyday life more remarkable through technologies that continually redefine life as we know it.

In my recent blog, titled “Paving the way for digital identities and mobile eGov access”, we discussed some of the trends driving the expansion of online access to government services, and noted the importance of using secure login technologies to make online access safer and more convenient. In particular, we talked about how a digital ID, called a derived credential, can make the online login process safer, more flexible and more citizen friendly.
In this blog, we take a closer look at what derived credentials mean for an increasingly important subcategory of online government services – mobile government.
What is mobile government?
Mobile government, which is sometimes referred to as mGovernment or simply
mGov, is a rapidly expanding segment of online government services. It refers
to the use of smartphones and other mobile devices, running mobile apps or
using mobile web sites, as the access point to government information and
services.
The growing presence of mobile devices in everyday life, has led local, state and national governments to use mGov as an access channel to reach citizens and as a new way for citizens to reach government. Mobile devices enable government-to-citizen transactions, such as benefit payments, and can increase citizen participation by letting people provide input to political decision-making, including voting via mobile phones. The use of mobile devices can also improve the internal operation of public agencies, since it makes information easier to access and keep up to date.
It’s important to remember that mGov isn’t a replacement for other services, but can be a strong addition to eGov programs that are already in place. Similarly, the credentials used to access eGov/mGov services are not substitutes for traditional physical ID documents, such as birth certificates, driver’s licenses or marriage certificates. Physical documents remain the foundation of all government services – online or off – and remain the root credentials in case there are any problems with the network infrastructure associated with eGov/mGov services.
Challenges for mGov development
As a new subsegment of eGov, mGov faces many of the same challenges associated
with any emerging application. Perhaps most prominent among these are the
issues of cost, scope and trust.
To build trust within the stakeholder community, a rigorous development program, focused on the proper configuration of security mechanisms and supported device makers, can serve as evidence that the mGov program will meet the necessary requirements. Other government initiatives, including legislation to govern the proper use of mobile credentials, and communications campaigns that explain how security is managed by the mGov application, can help address end-user concerns and build trust, too.
eID – the root for a digital eIDAS
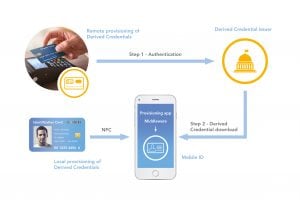
One thing that makes it easier to address the primary challenges of cost,
scope and trust is the use of proven and verified security technologies, such
as electronic IDs (eIDs). The use of standardized, time-tested eID formats
helps lower development costs, makes the deployment easier to scale and
increases stakeholder confidence.
The specific eID approach we recommend is to use a credential that is based on, or derived from, a primary credential. A primary credential is a form of identification issued on the basis of presenting a physical breeder document, such as a birth certificate. A national ID card, for example, is considered a primary credential, since it’s issued only after the citizen has passed a well-established process of identity proofing.
Using a primary credential as the source of the derived ID, the “root ID” is then held in a secure document. Additional IDs, derived from the root ID, can be generated for various end-user devices and can be stored either locally, in the device itself or remotely, in the cloud. Support for a broad range of devices helps maximize mobility for the most people, and adds convenience with inherent compatibility across devices.
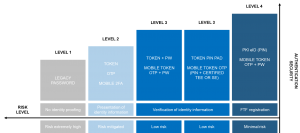
Choosing the right level of assurance
In the world of identity and access management, the level of assurance refers
to the degree of confidence that a credential is neither fraudulent nor
stolen, and that the person using the credential is the person to whom the
credential was issued. When granting access to any government service, the
level of assurance needs to meet the requirements of a given use case. A
low-risk transaction, for example, is likely to require a lower level of
assurance than a high-risk one. The security mechanisms supported by an
authentication platform typically dictate the level of assurance, and provide
a starting point for balancing the tradeoffs involved with risk, complexity and cost.
Extending smartcard-based services
Using digital credentials derived from smart card eIDs creates a smooth
transition to mobile formats. The mobile credentials are compatible with
existing contactless smart card infrastructures (including those that use
MIFARE or NFC), and can be authenticated using in-place methods. The mobile
device can quickly become an extension of in-place smart card eID programs that
already support things like user authentication, signing and decrypting email,
physical building access or in-store and Internet payments.
The NXP perspective
At NXP, we’re using our experience with eGov solutions to help drive
development in mGov. We’re working on a new service platform that will
provide the necessary infrastructure for digital authentication, including
support for derived credentials. We believe that, by using eID hardware as a
starting point, it will be easier to design and deploy secure authentication
services for mobile applications, and it will be easier to migrate
multi-application eID operation into the mobile space.
Next up: application opportunities
Once the secure, verified framework for derived credentials has been put in
place, government agencies can move quickly to reap the benefits of mGov
services. As one might imagine, given the flexibility and security made
possible by derived credentials, the number of applications is expanding
rapidly. We will address these new opportunities in our next blog.
Go a level deeper
To learn more about our work in this area, visit the eGov section of our
website or contact your local sales office.
Related links
NXP blog: Paving the way for digital identities and mobile eGov access
Tags: Security, Technologies

At NXP, innovation is always now, but our focus is always the future. Our dedicated team of experts is united by a passion to make everyday life more remarkable through technologies that continually redefine life as we know it.

April 11, 2019
by Kurt Bischof

September 11, 2019
by Mahdi Mekic

October 17, 2019
by Tim Daly